Beijing does not need to censor content posted online by its citizens first-hand; it has a retinue of corporate employees and individual nationalists to police domestically-generated internet content. Thus, the censorship technology authorities control more directly targets information seeping in from outside China. These tools perform “network-level censorship,” inspecting data headed across the border, regardless of which app or service generated it.
It’s easy to think of Beijing’s simply toggling a switch: internet on, internet off. Or, more specifically, this website on, that website off. In fact, the internet itself comprises many different components, each offering censors opportunities to disrupt or co-opt the information exchanged within that component. China’s day-to-day control mechanisms, therefore, function as more than simple on-off switches. Instead, they often hijack the internet’s normal functions and turn them against themselves.
We know about many of China’s network-level censorship tools thanks to experiments conducted by researchers located outside of the mainland. (Beijing, unsurprisingly, does not openly discuss the technical means it uses to disrupt internet traffic.) But how can someone outside China see how the government censors traffic inside China? Network-level experiments work, even from abroad, because the censorship system is mostly bidirectional. This means that the system largely doesn’t bother to check whether internet traffic is coming from inside or outside of China—if that traffic contains banned content, the system will censor it, no matter what direction it’s headed. Researchers have taken advantage of the system’s bidirectionality to test what content is actually banned.
Data Packets: The Basis of Internet Information Exchange
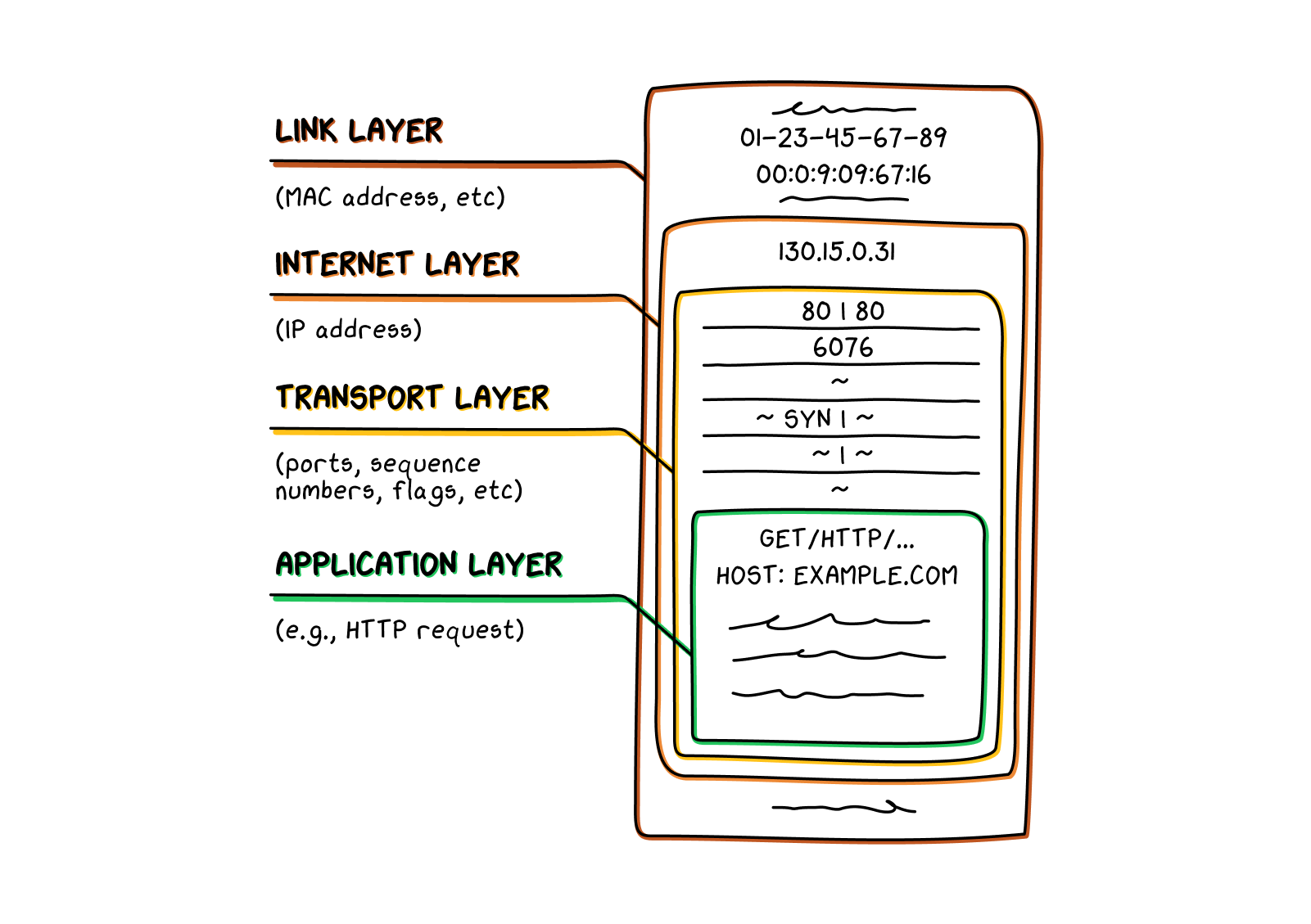
The internet’s basic functions depend on packets: small chunks of information, sent one by one across the network. The conceptual basis for the entire internet depends on packets. Breaking down information—such as an email or a text message—into pieces allows the network to send those pieces individually, along whichever of the many routes makes the most sense at the moment. Is there too much internet traffic between Beijing and Shanghai? No problem, just send a packet or two along a route that avoids those places.
Receiving a message over the internet is a little like getting a shipment from IKEA. But rather than sending you one parcel containing all the constituent parts for, say, a table, imagine IKEA instead sends you several separate parcels—one containing the table legs, one containing the table top, and one containing the screws needed to put them together. Each parcel looks identical on the outside, in the same size box, so no one shipping them from one place to another knows what’s inside them. The parcels arrive on different delivery trucks, with each driver getting different directions from her GPS about which route is the fastest to your home. The delivery trucks share the road with hundreds of other vehicles carrying their own parcels to different destinations. Your parcels might arrive at your home around the same time, or depending on the routes the delivery trucks took, could arrive over the course of the day. If one of the parcels goes missing, IKEA will send you a replacement. Once you receive all the parcels, you assemble them correctly to produce a table.
Information transmitted over the internet travels essentially the same way: whenever you send information, such as an email, your computer breaks the email down into packets. The packets contain fragments of the email—a sentence or two here, part of an image there—however much will fit inside the packet. Unlike in the IKEA example, in which you’d hope your table top arrives in one piece, your computer can easily break apart sentences, images, or anything else into small parts to fit into packets. The packets also contain some additional addressing information that helps guide them through the network to their intended destination. After your computer sends out these packets, the network will respond to real-time conditions and route them individually along whichever path seems most efficient at the time. Your packets are traversing the network along with packets from many other users—just like delivery trucks on a road, many different packets can share part of the same path even if their final destinations are different. Once the receiving computer gets the packets, it can determine whether any packets are missing and, if needed, your computer can resend them. The receiving computer then reassembles them in the proper order, and the recipient can read your email.
The internet, as a “packet-switched” network, represents a massive innovation over “circuit-switched” networks, like landline telephone networks. On landlines, at least historically, a dedicated circuit is established between a caller and a receiver. That circuit remains the same for the duration of the phone call, and no other callers can use it (otherwise you’d hear their voices on the line as well). This setup severely limits how much information can traverse a circuit-switched network; the number of possible circuits determines the maximum number of phone calls that can happen at any one time. In the IKEA analogy, this would be tantamount to shutting down roads to all but one delivery vehicle at a time.
On the internet, by contrast, because packets can mingle along the same route, the limiting factor is the number of packets a cable can carry, not the number of person-to-person connections. Thus a packet-switched network can handle much more information much more quickly than a circuit-switched network can, allowing for all of the wonderful, terrible, and downright frivolous real-time applications humans have developed for the internet.
Censorship Built into the Infrastructure
China’s control over this process begins before any
packets
The physical infrastructure also includes built-in chokepoints for international internet traffic. The People’s Republic of China (PRC) has relatively few international gateways—especially as compared to other technologically developed states such as Singapore, the United States, or Japan—with just a few companies running them. One study, estimating the “national chokepoint potential” of various countries in 2018, found that China sat at one extreme of the spectrum: only two
ISPs
The “chokepoint potential” of this system offers both the government and the state-owned
ISPs
IP Blocking
The internet depends on IP (
Internet Protocol
All websites have an
IP address
When a computer divides information into
packets
Routers are akin to post offices or carrier facilities that receive parcels in transit and forward them on to another facility closer to their destination. Each post office along the way might ship the parcel in the exact direction of the destination, if there is a post office there to receive it. Or, it might decide to ship the parcel slightly out of the way—if, say, a road had been washed out or was gridlocked during rush hour. Routers have similar information about the networks around them and dispatch packets along the best possible path at the time, avoiding any damaged or congested paths. This means that the packets from one email or text might take different paths, maybe transiting dozens of routers, before arriving at the recipient’s device.
If someone in China is trying to visit a blocklisted website hosted in the United States, his computer attempts to send a packet to the website, containing something akin to “Hello! I’d like to connect!” The packet travels from the computer, through a series of routers, each of which reads the
IP address
It does this essentially by claiming the U.S. website is inaccessible, even though that’s not actually true. The Chinese government (or a company working at its behest) has loaded false information onto these international gateways, alleging IP addresses associated with “dangerous” websites or services are unreachable. When a router near the border, trying to figure out how best to route a packet to the U.S. website, asks the international gateway for information, the international gateway will tell the router that the website in question can’t be accessed. The router will then simply give up, not bothering to forward on the packet. The user in China might get an error message like “Network unreachable” or “Connection refused.” To return to the post office example, this would be like a postal worker calling the next county over to figure out the best route for a particular parcel, only for the person on the other end to inaccurately tell them the destination address no longer exists. Rather than sending the parcel back to its point of origin, the postal worker just dumps the parcel into a garbage bin.
This means of online censorship is known as “IP blocking,” and China has employed it for nearly as long as the country has been connected to the internet. As a censorship technology, it is cheap and easy: it requires no special hardware, as authorities can simply alter the information stored on existing routers and
international gateways
Back in the late 1990s, when there were dozens of independent ISPs providing internet access throughout China,
ISPs
In 2019, one study determined that Chinese authorities were using IP blocking against nearly 40,000 of the one million most popular global websites. They likely block far more than just these 40,000; many of the websites China’s Party-state wishes to block are far more niche and likely wouldn’t appear among the web’s most visited sites. Notably, however, authorities do not block all websites this way; they have a number of additional technologies they use to block other sites—and sometimes one site can be blocked by multiple different technologies. Authorities likely use IP blocking against sites and services with relatively static IP addresses.
Even though IP blocking represents an older generation of censorship technology, it’s still very much a key weapon in China’s online censorship arsenal. It works in tandem with an expanding set of additional blocking technologies, most of which require supplemental, specialized hardware, known as “middleboxes,” to identify and block internet traffic the CCP deems threatening. Like IP blocking, these technologies depend on computers throughout the network to behave according to commonly-accepted practices, which the technologies then subvert to their own ends. And, like IP blocking technologies, these middleboxes are physically located near China’s national borders, to better patrol the internet traffic entering and leaving the country.
Blocking via Middlebox
In the China context, middleboxes serve as little digital spies embedded in the online network. They are actual, physical pieces of hardware that inspect
packets
In most cases, the government’s middleboxes don’t bother to stop an initial packet or two from flowing across the border. Instead, equipment near the border makes copies of those packets, allowing the original packets to continue on to their intended destination, and sending the copies to a middlebox. The middlebox then inspects the copies, and if it finds objectionable content, takes steps to temporarily stymie any further communication between the sender and the destination.
This method may seem unnecessarily circuitous. Why shouldn’t the Chinese government simply stop the original packets from ever crossing the border and just end the whole business right there? Though there are a few cases when middleboxes do stop the original packets, the copy method remains much more widely used because it saves resources and money. A middlebox that has to read packets and make decisions about them in real time requires a fair amount of computing power if it wants to keep internet traffic running smoothly and quickly.
Imagine a cash-strapped secret police station that wants to prevent citizens from sending letters and parcels back and forth to certain foreign “enemies.” In particular, they’re very concerned with keeping citizens from getting politically inconvenient information from the outside world. At the same time, however, the country depends on international commerce, so the secret police do not want to stop or even significantly slow down innocuous mail from flowing through the system. If the secret police hoped to review all the mail headed across the border in real time, they would need to hire many additional officers, particularly during busy hours of the day, when the volume of mail could easily overwhelm a small workforce. This would allow them to immediately throw out any parcels they found concerning, but it would cost much more in salaries and office space.
The analogy breaks down a bit here, but if we can permit the use of a little magic, it can still help explain how the copying mechanism works. Let’s assume the secret police have a cheap, fast way to copy all of the mail flowing through the system, and one that doesn’t require hiring a bunch of additional officers. (Perhaps they have a sorcerer’s apprentice on staff, who, upon enchanting individual parcels, can then split them in half and thereby create a second version of each parcel.) The secret police could then allow the original mail to continue unimpeded across the border, while sending all the copies for inspection and review. The mail reviewers would still work quickly, but they would have the benefit of a little extra time—they would know the original parcel still has to travel all the way to its foreign destination, whereby the recipient would have to compose and send a reply, which would then have to make its way back across the border, all before any citizen could conceivably get their hands on it. This gives the secret police enough time to spring into action and take whatever steps they so choose to prevent further communications between these two individuals.
The effectiveness of this method lies in the physical location of the
middleboxes
DNS Blocking
Middleboxes
Let’s say that Xiaofang in Shanghai wants to visit a blocklisted website in the United States. When she types the domain name into her browser (“nytimes.com”), her computer sends out a
packet
The middlebox will see the requested domain name and compare it to a blocklist of banned domain names. Finding “nytimes.com” is on the blocklist (we’re assuming for the sake of this example that The New York Times is blocked by
DNS
This method works, even though Xiaofang’s DNS request likely did generate a real answer from The New York Times’
server
China probably started using DNS blocking in late 2002. Two decades later, according to tests conducted by researchers on 600 million domain names, Chinese authorities were blocking about one million websites via
DNS
Deep Packet Inspection
But
middleboxes
In the IKEA analogy, a computer creating packets is like IKEA shipping a table by breaking it up into constituent parts (legs, tabletop, screws), packaging each part separately, and sending them individually to the receiver. This is correct as far as it goes, but it leaves out a crucial part of packet creation: encapsulation. Imagine that instead of one box, each table part is put into a series of four nested boxes, with the innermost box showing the recipient’s name and containing one of the table parts. The outer boxes all have their own information written on them (one might have the zip code, for example), but none gives any indication of what might be inside. While this parcel is in transit, whoever handles it may see only the outermost box, or they may open it to view what’s written on the second- or third-largest box to help decide where to send the box next. But only the final recipient is supposed to get all the way to the inner box, seeing their own name on the outside and opening it to find what it contains.
This is also how packets work over the internet, with the actual substantive content (say, a few lines of an email) nested in the innermost part of a packet, invisible to the network until it reaches the intended recipient. The outer layers of a packet contain information to aid in routing and other tasks, but generally give no clue as to the actual content of the packet. A
middlebox
Neither IP nor DNS blocking require
deep packet inspection
HTTP Blocking
HTTP blocking targets the Hypertext Transfer Protocol (HTTP), the foundation for internet communication. The protocol acts as a set of instructions for requesting information from a website (or other online resource), as well as sending and receiving that information. You probably recognize it as the first part of many web addresses: “http://www.example.com.”
Let’s say Tianyu in Guangdong wants to visit a webpage hosted in the United States. This (fictional) webpage, “www.cnbc.com/falungong.html,” hosts a CNBC article about the banned spiritual group Falun Gong. The CNBC domain (“cnbc.com”) appears on neither China’s DNS blocklist nor IP blocklists, but the full URL does contain a phrase that the Party-state generally wishes to censor: “Falun Gong.”
After Tianyu types “cnbc.com/falungong.html” into his browser, his computer sends out
packets
This is when the middlebox springs into disruptive action. The middlebox must terminate further communication between Tianyu and “www.cnbc.com/falungong.html,” even as Tianyu’s original packets are still en route to the website. The middlebox does so by issuing its own “reset” packets to both Tianyu and “www.cnbc.com/falungong.html.” Reset packets do exactly what they say: they tell the recipient to disconnect (reset) the connection. Upon getting these reset packets, both Tianyu’s computer and the machine hosting “www.cnbc.com/falungong.html” will adhere to internet norms and break off their connection.
Again, the physical location of the middleboxes inside China makes this method possible. Even if “www.cnbc.com/falungong.html” manages to issue a response to Tianyu, the middlebox’s reset packets will almost certainly reach Tianyu’s computer first. Tianyu’s computer will faithfully reset the connection, and when the “www.cnbc.com/falungong.html” packets arrive, his computer will simply refuse to take them.
Worse yet, if Tianyu tries to reconnect to “www.cnbc.com/falungong.html” the middlebox will enforce what is called “residual censorship.” For a minute or two after resetting a connection, a middlebox monitors the network for any additional connection attempts between the same two endpoints (that is, between Tianyu’s computer and cnbc.com), and will issue additional reset packets if it detects such an attempt. Residual censorship likely aims to tacitly train internet users in China not to even bother trying to access certain websites or information about certain topics.
These three intertwined technologies—conducting keyword filtering of domain names via
deep packet inspection
Though keyword filtering has been in use in China for over two decades, the Party-state continues to invest in its improvement. For example, in the first few years of their deployment, the keyword-filtering middleboxes couldn’t keep track of the back-and-forth exchange of packets within any given connection, and their reset packets contained a number of tells indicating that they had been forged by middleboxes. This meant that tech-savvy users could potentially evade the system by simply ignoring reset packets that had obviously been generated by a middlebox. But by 2009, authorities had begun to deploy equipment that could conduct connection tracking—even though such tracking entails more computing resources and therefore money—and by 2011 the entire system had been upgraded to more closely monitor each individual cross-border connection. By then the middleboxes had also already begun to send more convincing reset forgeries. These developments both helped make the system harder to sidestep. Even so,
deep packet inspection
In addition to operational enhancements, authorities have also (apparently) discontinued at least one major function of the keyword-filtering system. The system used to inspect not only the domain names written to packets but also the contents of the packets themselves, such as the text of a website or email. (In the four-nested-IKEA-boxes analogy, this is equivalent to opening the innermost box and looking at what’s inside.) As one might imagine, this is a relatively slow, resource-intensive process—and one that, in practice, had a high failure rate—perhaps leading the Party-state to abandon it.
But one of the most important, if still narrowly implemented, conceptual changes to
network-level censorship
In recent years, however, the Chinese government has made use of its network-level censorship system to keep international internet users from accessing information inside China. Its tweaks to the
DNS
HTTPS Blocking
Of course, internet technologies, particularly privacy- and security-related technologies, haven’t been standing still either. Over the last 20 years, developers have worked to integrate encryption into the world’s everyday internet browsing. This started with the introduction of HTTPS (a more secure version of the protocol your computer uses to connect to a website, and what you’ll see at the left of your browser’s address bar as you’re reading this article). HTTPS encrypts the innermost layer of each
packet
The uptake of HTTPS did briefly hinder China’s
network-level censorship
Internet engineers then upped the ante by encrypting this field, creating “encrypted server name identification.” This innovation threatened to negate the bulk of China’s network-level censorship—there was just no easy way to read an encrypted server name identification field. It alarmed Beijing enough that, since mid-2020, authorities have simply blocked any packet (and therefore any connection) that makes use of encrypted server name identification, even though ESNI never ended up being widely deployed globally.
Blocking an entire technology wholesale represents a significant shift in censorship tactics. Previously, China’s censors had resigned themselves to disregarding internet traffic they didn’t have the ability to censor, judging that the downsides of “blocking all” outweighed the risks of “blocking none.” But because encrypted server name identification had not yet been widely adopted, officials clearly felt they could take this step without causing too much economic pain.
Network-level censorship can therefore block both specific websites and specific technologies, helping the Party-state keep out “dangerous” information they already know about as well as potentially “dangerous” information they can’t read. In this way, it also assists with the larger project of meta-censorship. The Google Play Store, for example, is unavailable in China due to both DNS blocking and keyword filtering; anything a Chinese user might download from the Play Store is also unavailable. This saves Beijing from having to individually evaluate all the apps posted to Google Play (which doesn’t have the same sort of top-down approval process that Apple’s App Store does). Instead, simply blocking “google.com” ensures that the chaotic, unvetted mass of conceivably subversive software stays safely out of China’s cyberspace.
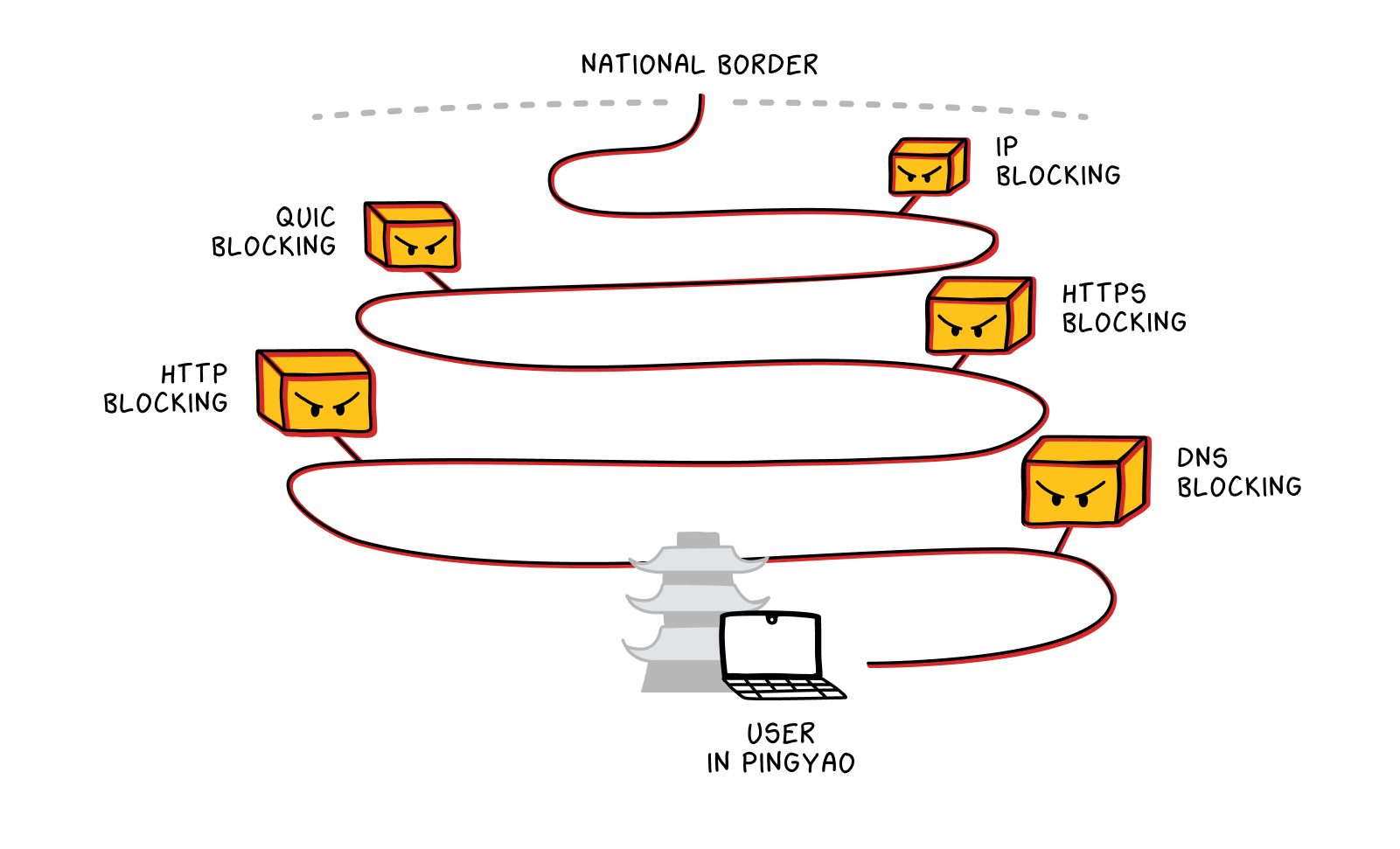
Data packets leaving China must run a gauntlet of middleboxes (including middleboxes targeting the QUIC protocol).
